public key cryptography & rsa Algorithm
Public key Cryptography:
In public key cryptography there are two keys: a Private key and a Public key.The Private key is kept by the receiver. The Public key is announced to the Public. It is also known as Asymmetric Key Cryptography.
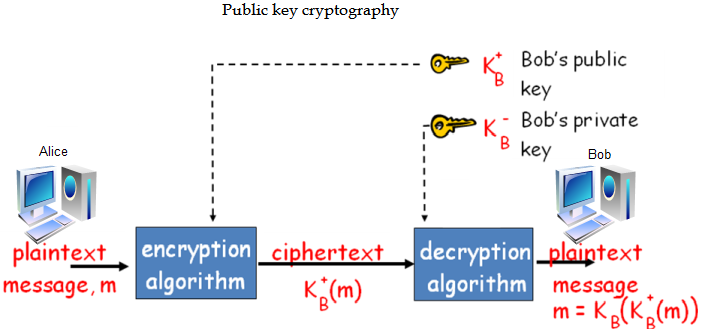
=> Alice generates a key value (usually a number or pair of related numbers) which she makes public.
-
=> Alice uses her public key (and some additional information) to determine a second key (her private key).
- => Alice keeps her private key (and the additional information she used to construct it) secret.
- => Bob (or Carol, or anyone else) can use Alice’s public key to encrypt a message for Alice.
- => Alice can use her private key to decrypt this message.
- => No-one without access to Alice’s private key (or the information used to construct it) can easily decrypt the message.
One-way functions:
Public key encryption is based on the existence of trapdoor one-way functions.
~ Encryption with the public key is easy.
~ Decryption is computationally hard.
~ Knowledge of the private key opens the trapdoor, making inversion easy.